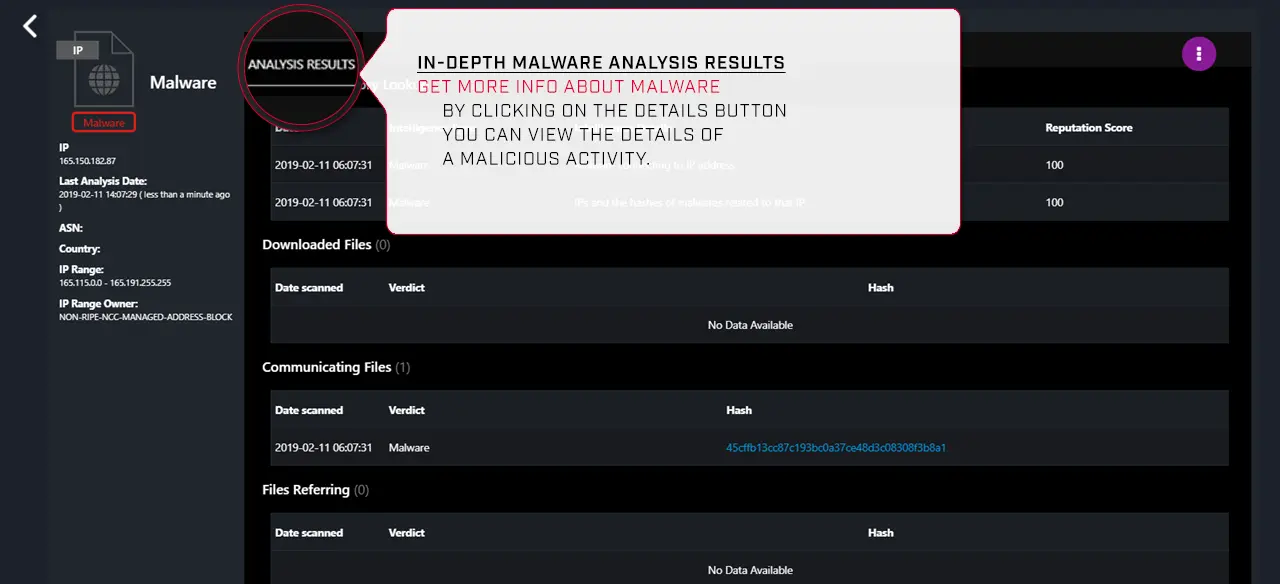
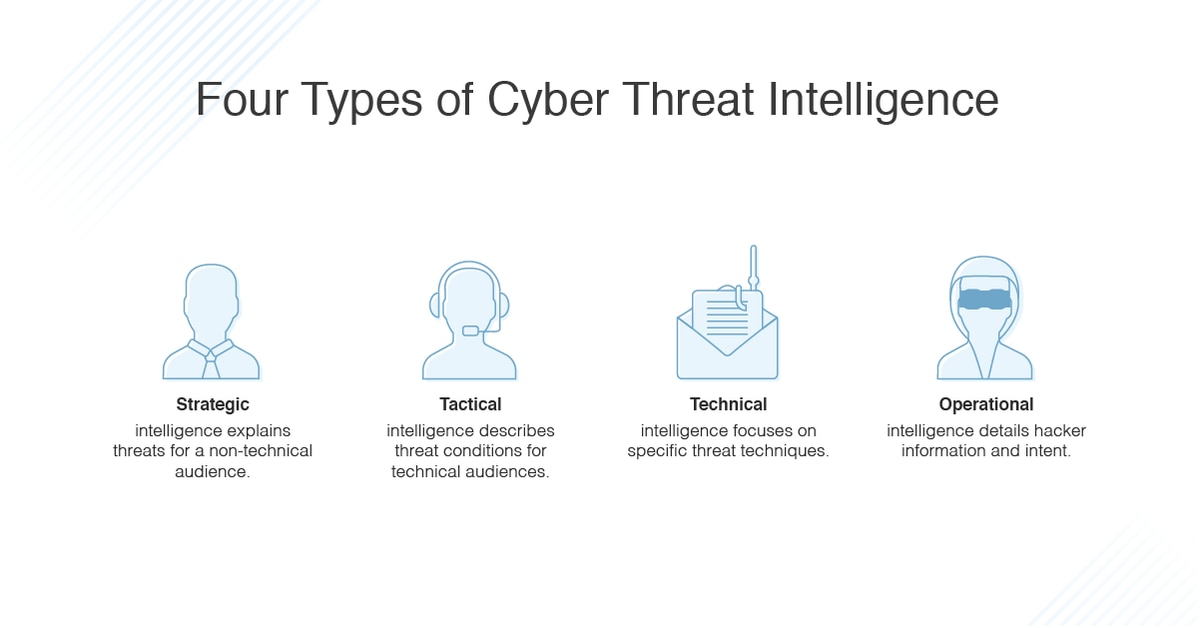
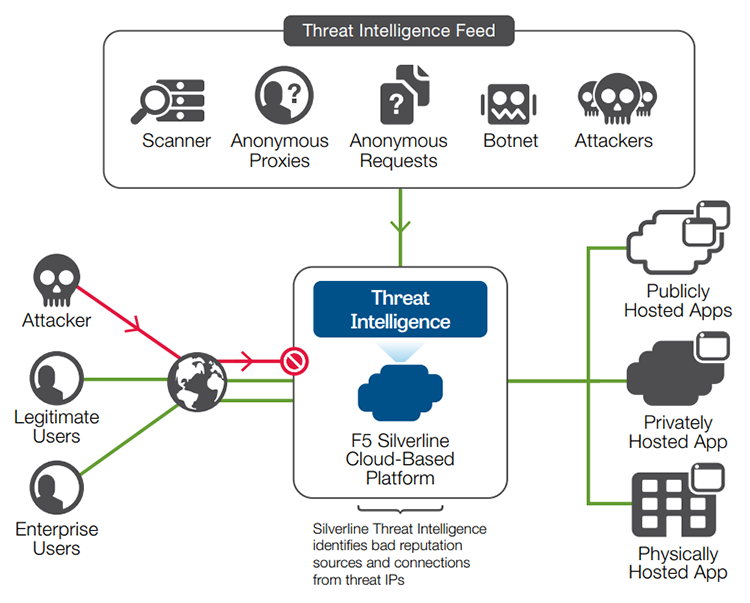
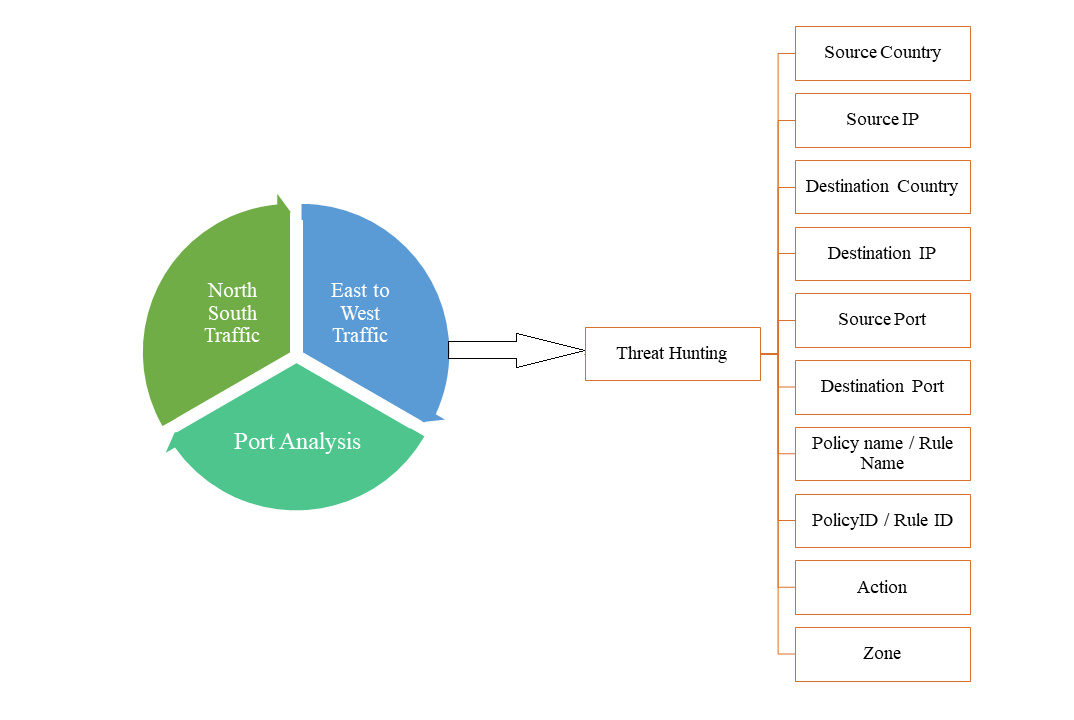
Unified value: enhanced TI Portal provides consolidated access to Kaspersky Threat Intelligence expertise | Kaspersky

Threat Analysis System - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

![What Is IP Reputation And How To Check It? [Updated 2022] What Is IP Reputation And How To Check It? [Updated 2022]](https://www.vpnranks.com/wp-content/uploads/2022/02/brightcloud-ip-detection.png)