Sosyal Mühendislik Yöntemiyle Kurban Bilgisayarına Shell Açma - Bölüm-1:Saldırı Kodunun Hazırlanması ~ BTRiskBlog Pentest, ISO27001 ve BT Denetimi Hakkında Her Şey
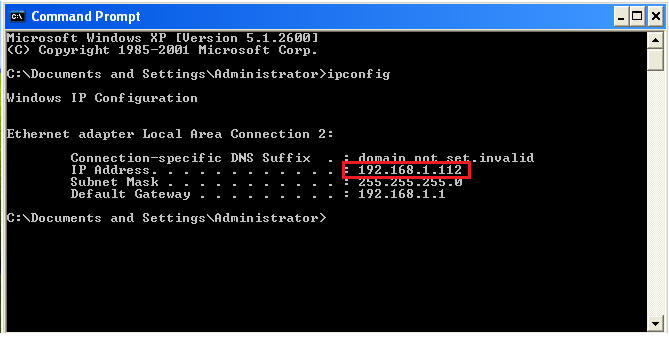
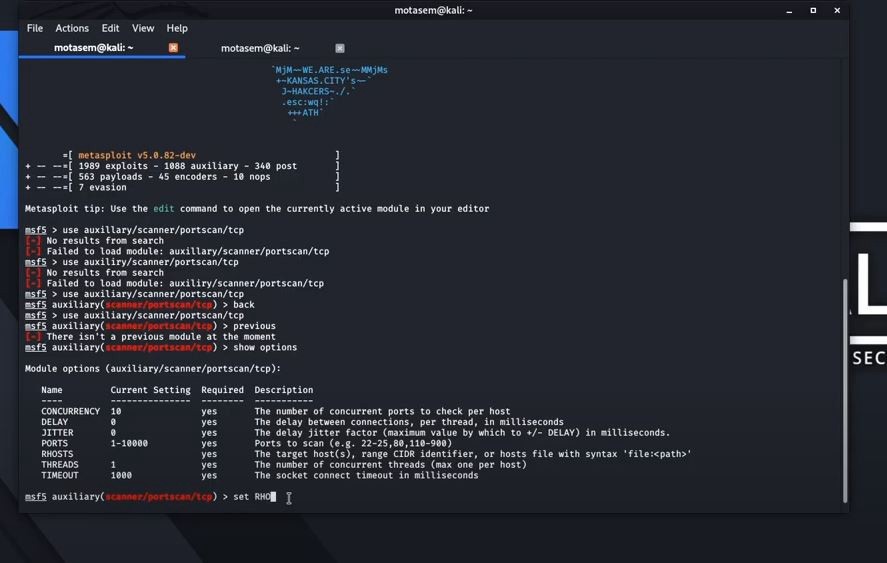
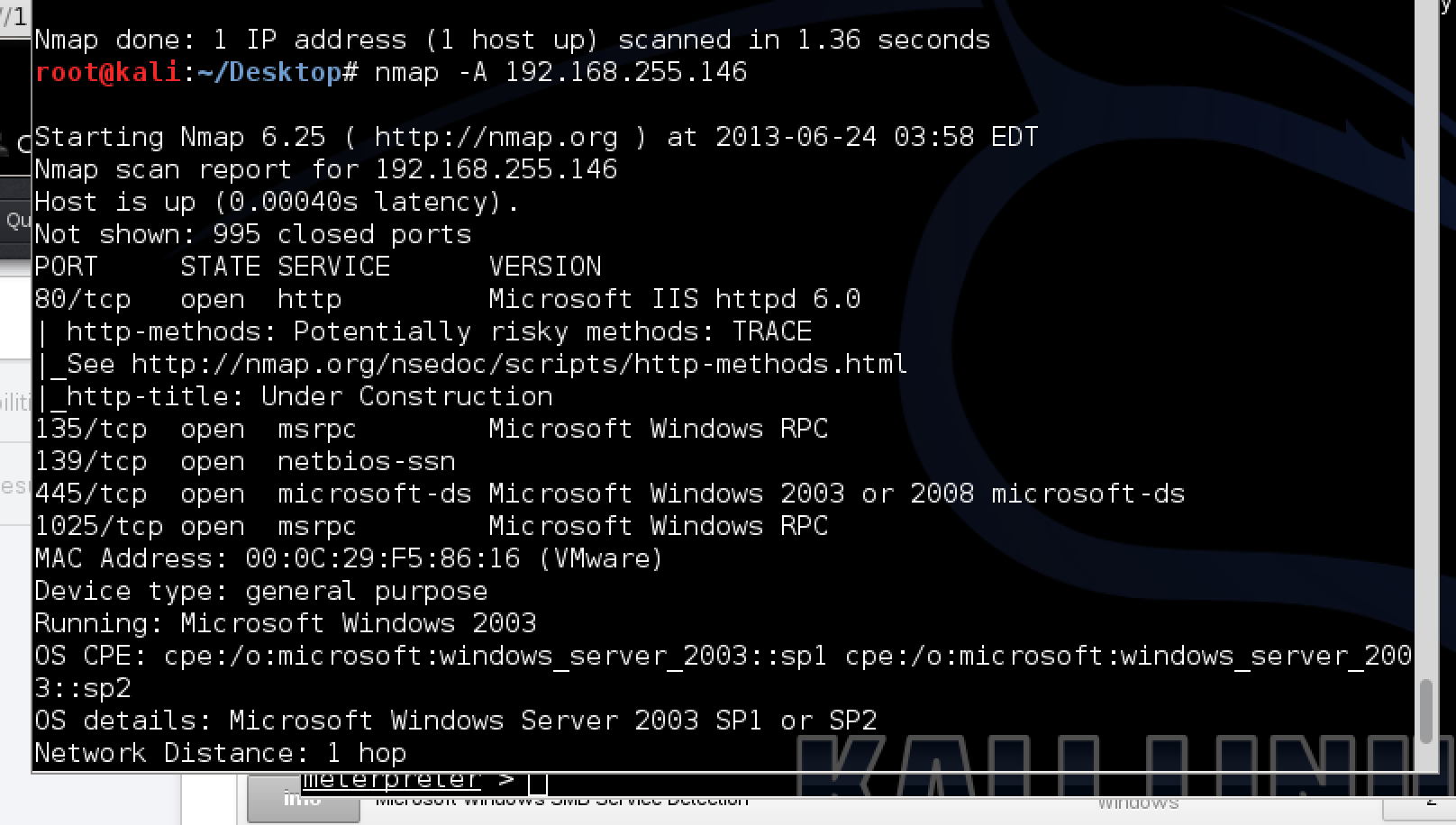
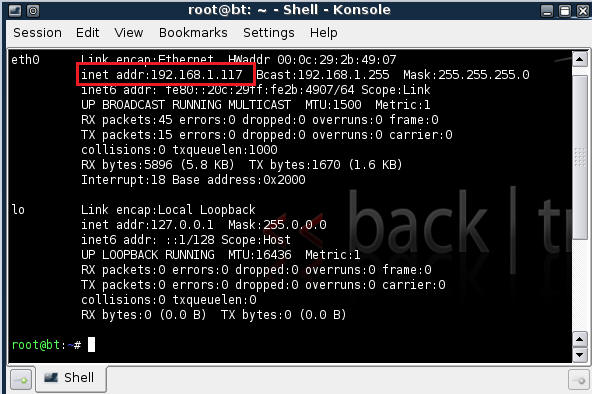
![Metasploit Tutorial] Hacking Windows XP using IP Address – Ethical Hacking Tutorials | Learn How to Hack | Hacking Tricks | Penetration Testing Lab Metasploit Tutorial] Hacking Windows XP using IP Address – Ethical Hacking Tutorials | Learn How to Hack | Hacking Tricks | Penetration Testing Lab](http://3.bp.blogspot.com/-3e7h8O4zDy4/UAGismUDWnI/AAAAAAAAA1Q/ErXnb4uiiWA/s1600/Metasploit_Tutorials_2.jpg)
Metasploit Tutorial] Hacking Windows XP using IP Address – Ethical Hacking Tutorials | Learn How to Hack | Hacking Tricks | Penetration Testing Lab