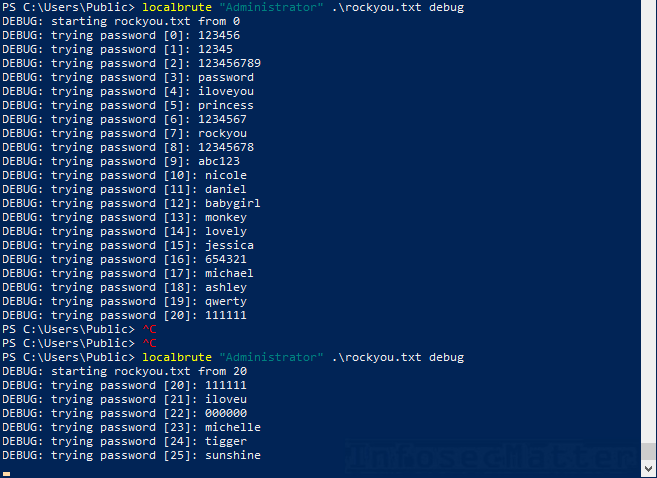
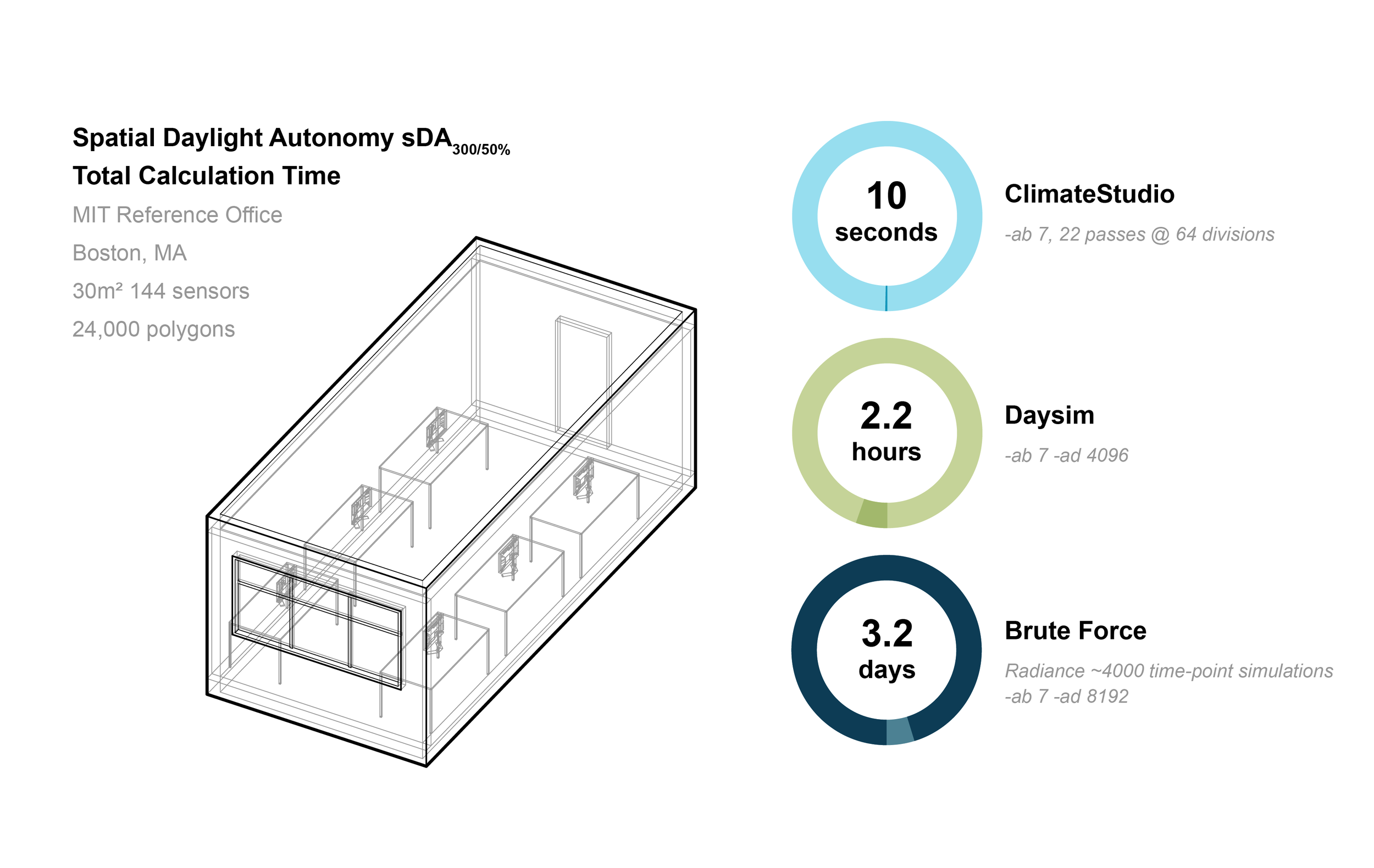
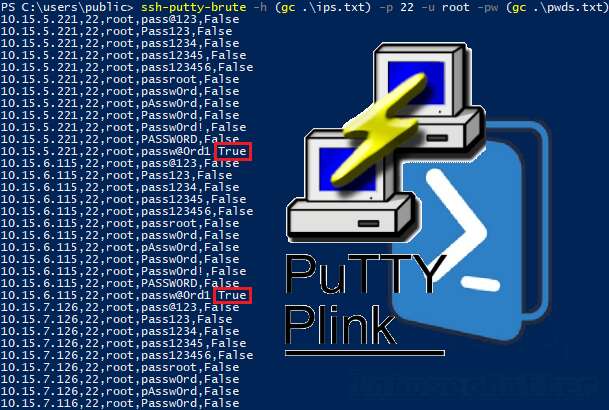
Brute force simulation accuracy vs. number of steps in the simulation.... | Download Scientific Diagram

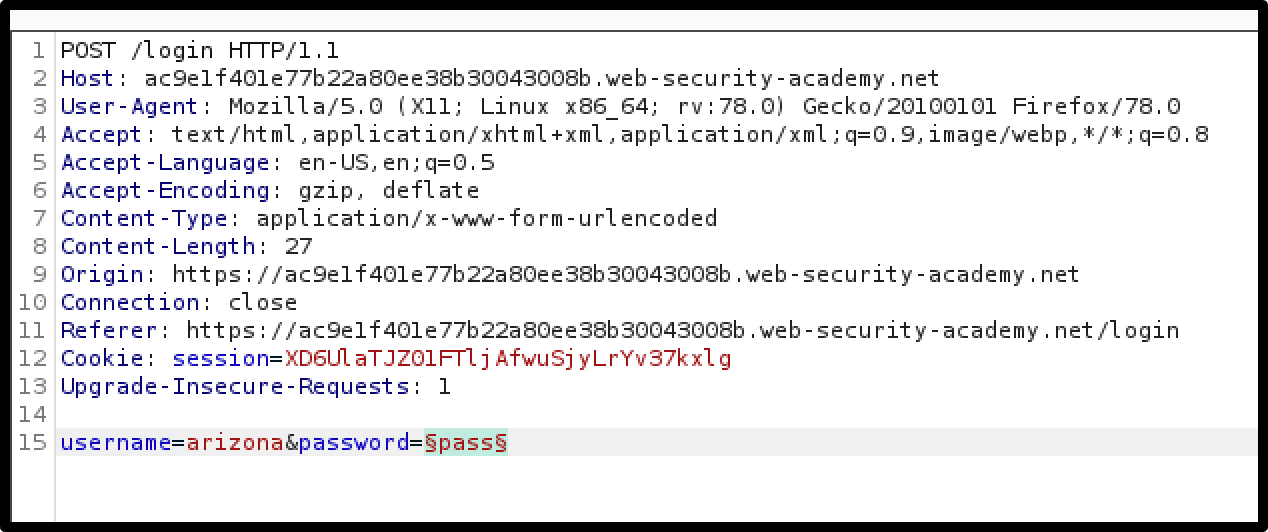
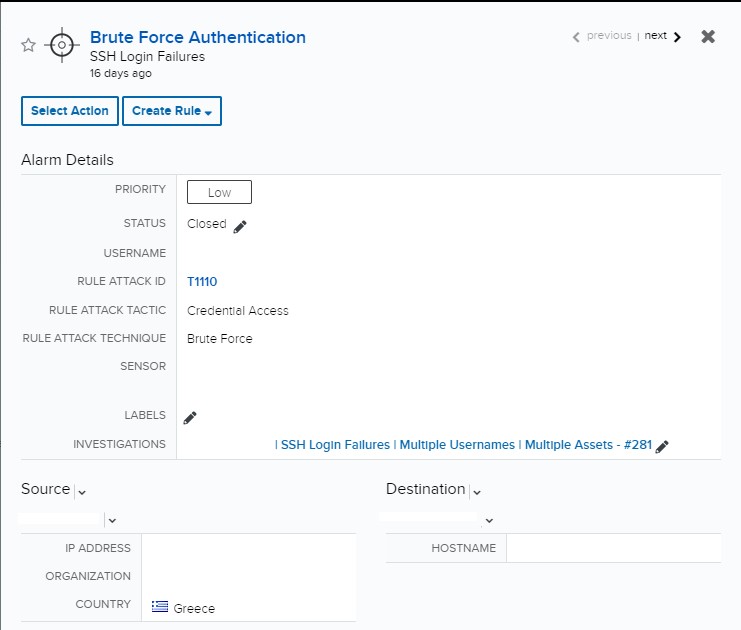
Data science for cybersecurity: A probabilistic time series model for detecting RDP inbound brute force attacks - Microsoft Security Blog
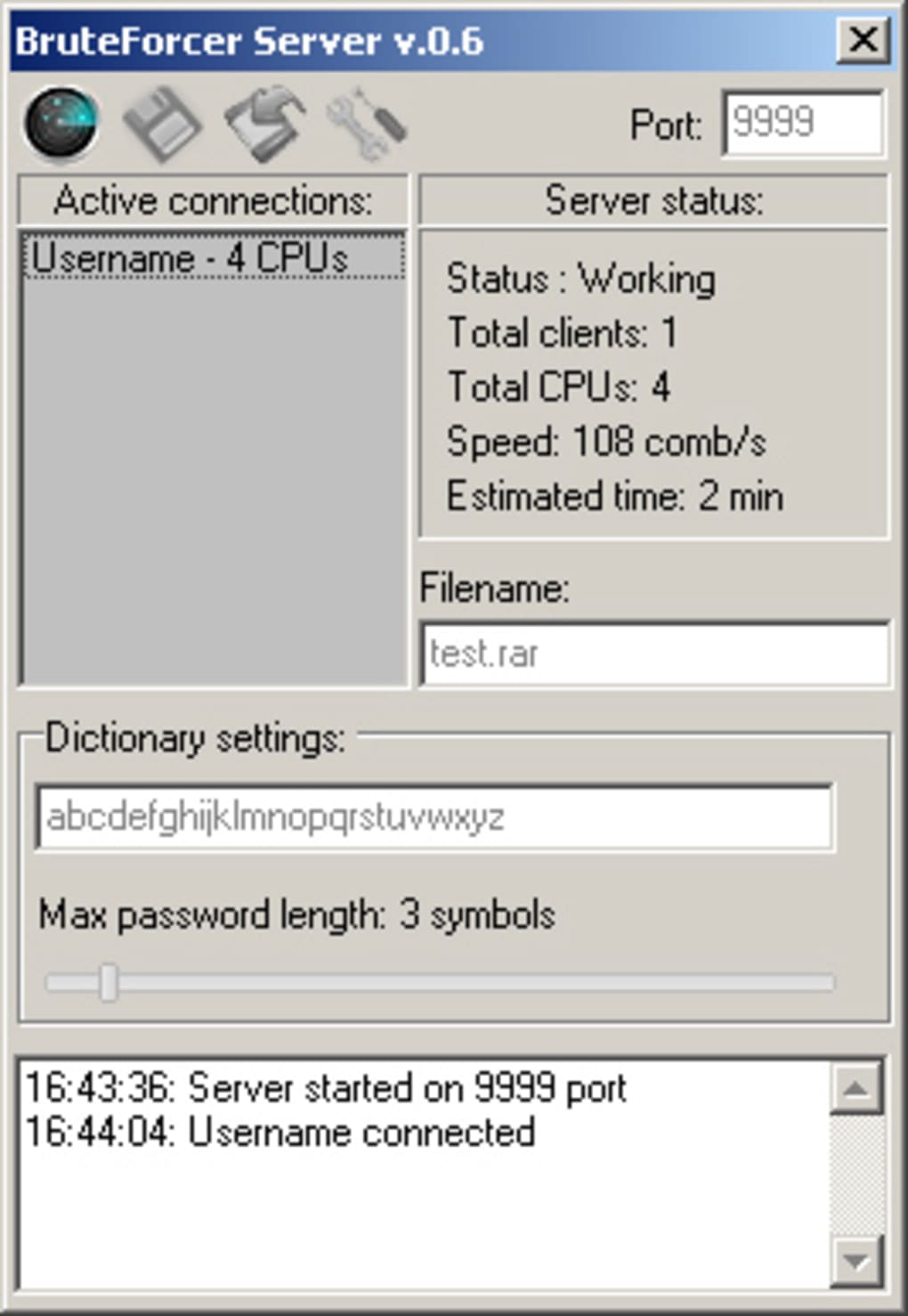
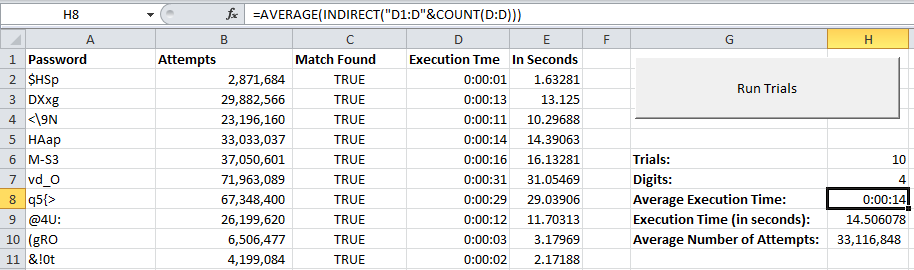
Time taken for sub brute force attack Another simulation is conducted... | Download Scientific Diagram
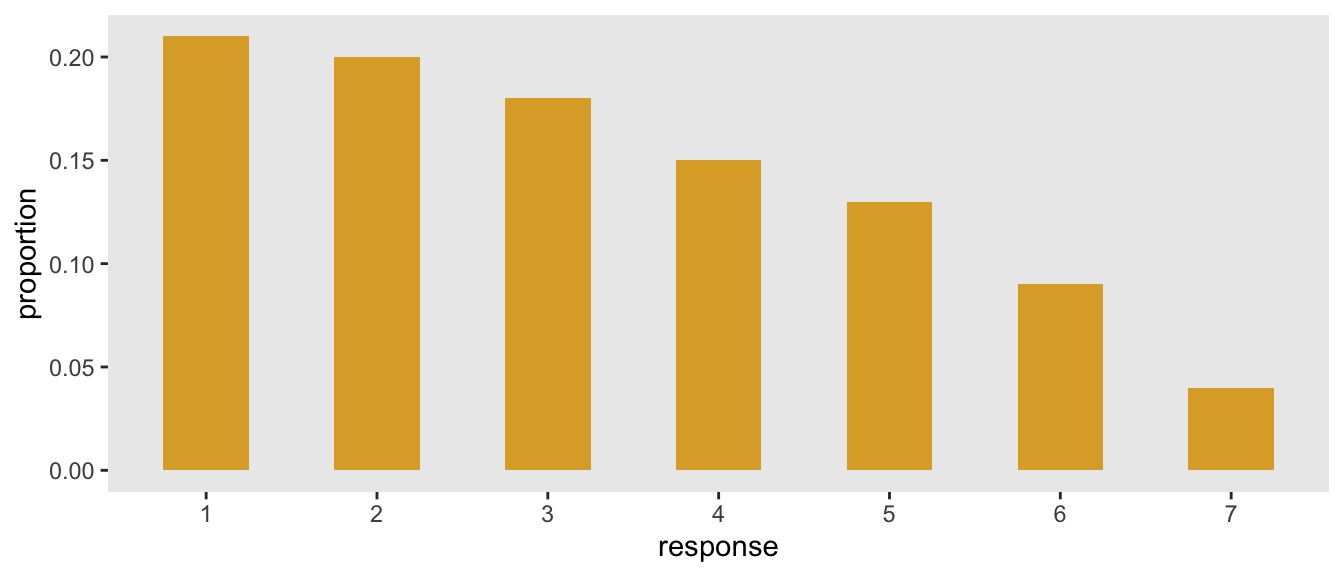
How long would it take to brute force a 8-character password with an IBM Summit supercomputer? - Quora